How to Fix “550 5.7.520 Access Denied, Your Organization Does Not Allow External Forwarding” in Office 365
External email forwarding is a common requirement for many organizations — whether for shared mailboxes, ticketing systems, or users who need to receive mail on external accounts. However, Microsoft 365 (formerly Office 365) blocks automatic external forwarding by default to protect organizations from data leaks and compromised accounts.
If you try to forward emails externally and see this error:
Remote Server returned:
550 5.7.520 Access denied, Your organization does not allow external forwarding. Please contact your administrator for further assistance. AS(7555)
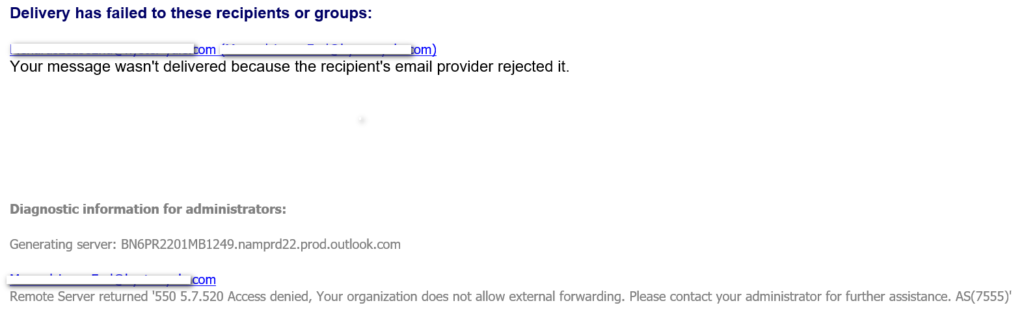
…it means your outbound spam policy is blocking automatic forwarding.
This guide explains why the error occurs, how to enable external forwarding, and what security considerations you should keep in mind.
Why External Forwarding Is Blocked by Default
Microsoft blocks external forwarding because:
- Compromised accounts often auto‑forward emails to attackers
- Sensitive data can leak outside the organization
- Forwarding rules are commonly used in phishing attacks
- It helps reduce outbound spam from hacked mailboxes
To allow forwarding, you must explicitly enable it in the Outbound Spam Filter Policy.
How to Enable External Email Forwarding in Microsoft 365
Follow these steps to allow automatic external forwarding for your organization.
Step 1: Open the Microsoft 365 Defender Portal
Open the Microsoft 365 Defender Portal
or navigate manually:
Open https://security.microsoft.com
Email & collaboration → Policies & rules → Threat policies → Anti‑Spam
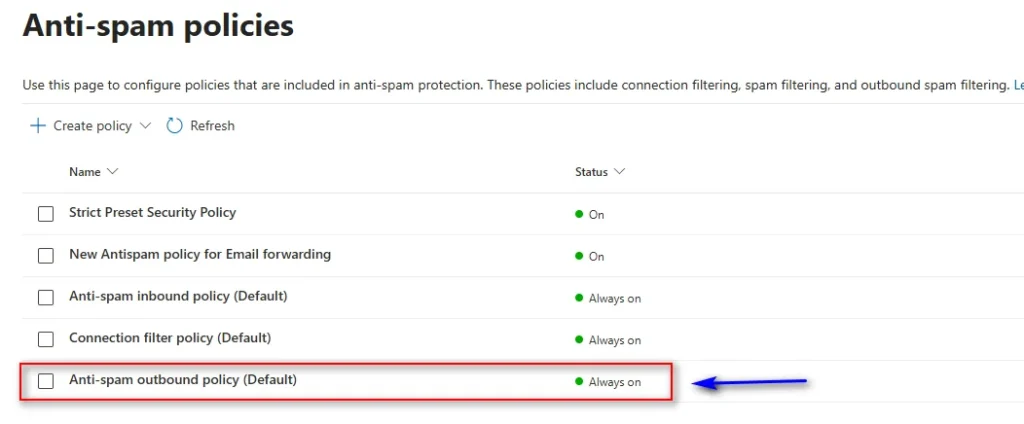
Step 2: Edit the Outbound Spam Filter Policy
- Scroll down to Outbound spam filter policy
- Select Anti-spam outbound policy (Default) (or your custom policy)
- Click Edit policy
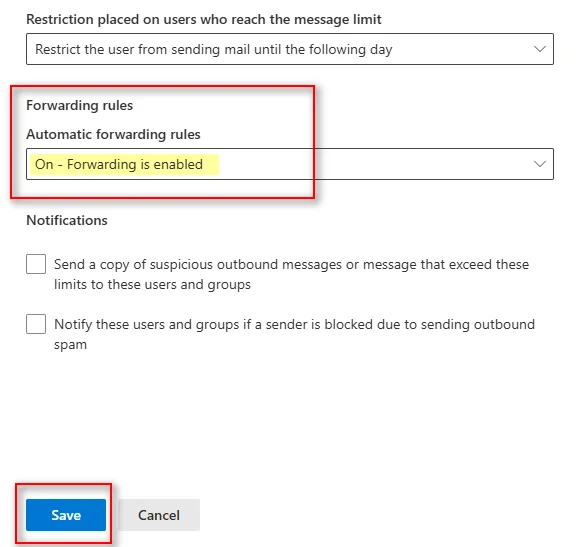
Step 3: Enable Automatic Forwarding
Inside the policy settings:
- Expand the Automatic forwarding section
- Select:
✅ On – Forwarding is enabled
- Click Save
This allows users to forward emails to external recipients.
Step 4: Wait for Policy Propagation
Changes can take up to 60 minutes to apply across Microsoft 365.
After propagation, external forwarding should work as expected.
Optional: Allow Forwarding for Specific Users Only
If you don’t want to enable forwarding for the entire organization, you can:
Option A — Create a custom outbound spam policy
Apply it only to selected users or groups.
Option B — Use an Exchange Online transport rule
Allow forwarding only for specific mailboxes.
This is more secure and recommended for most organizations.
Troubleshooting Tips
If forwarding still doesn’t work:
✔ Check the mailbox forwarding settings
Microsoft 365 Admin Center → Active Users → Mail → Manage email forwarding
✔ Check Outlook inbox rules
Users may have conflicting rules.
✔ Check if the mailbox is compromised
Look for unusual forwarding rules or sign‑ins.
✔ Check your tenant’s outbound spam limits
High‑risk users may be blocked.
Security Best Practices for External Forwarding
External forwarding increases risk. Follow these guidelines:
- Enable MFA for all users
- Use Conditional Access policies
- Monitor outbound mail flow
- Enable alerting for suspicious forwarding rules
- Limit forwarding to trusted domains only
- Regularly audit mailbox rules
Final Thoughts
The “550 5.7.520 Access Denied” error is a common issue in Microsoft 365, especially in tenants with strict security policies. By adjusting the outbound spam filter policy, you can safely enable external forwarding while maintaining control over your organization’s email security.
